Scenario-based learning that measures real capability
Most learning platforms measure what people consumed. Nano Masters AI measures what people decide. Learners practice realistic situations—under pressure, with ambiguity—so you can verify readiness with evidence, not completion.
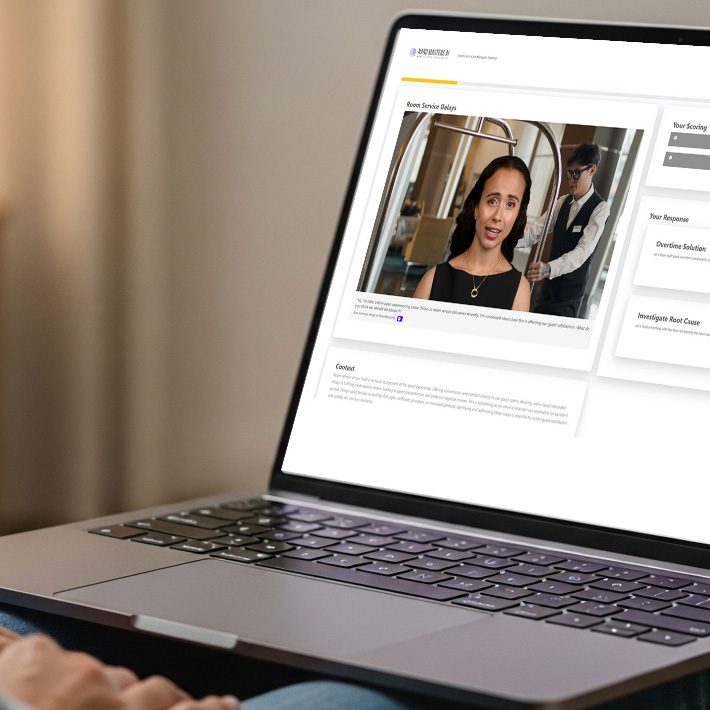
How scenario-based learning works
Nano Masters AI generates short, repeatable scenarios aligned to your role context and rubrics. Learners respond to ambiguity and trade-offs, and each response generates structured evidence.

- Scorecards by competency
- Common failure patterns
- Readiness signals by cohort
- Clear coaching priorities
Learning use cases
Designed for capability development where decisions and conversations define outcomes.
Leadership development
Practice feedback, delegation, conflict, and prioritization with measurable rubrics.
Soft skills at scale
Communication, feedback, and stakeholder alignment through short, repeatable scenarios.
Customer conversation practice
Discovery, de-escalation, and service recovery with structured coaching signals.
Manager coaching & feedback practice
Build manager confidence through repeated practice of 1:1s and performance conversations, supported by clear rubrics and actionable signals.
Crisis & escalation simulations
Train for high-pressure moments: rapid decisions, escalation paths, and stakeholder alignment— with evidence you can compare across cohorts.
From learning activity to capability evidence
Nano Masters AI helps L&D teams answer the question most platforms can’t: Did anything actually change? Measure improvement over time, identify coaching priorities, and make readiness decisions with confidence.